Remember those tumbleweed days when attracting clients felt like rolling a boulder uphill? Endless cold calls, emails that disappear into the void, and networking events that leave you feeling like a lone wolf. But fear not, fellow entrepreneur! There’s a secret weapon waiting to turn your website into a client magnet: SEO.
Imagine Your Website as a Neon Oasis in the Digital Desert
Before SEO, your website was like a hidden oasis in the middle of nowhere. Great if someone randomly stumbled upon it, but otherwise, crickets. SEO is like erecting a giant neon sign that screams, “Hey, I’ve got the solutions you crave!” right on Google’s bustling main street. Now, whenever someone searches for what you offer, your website pops up front and center. It’s like having a constant flow of thirsty travelers wandering in, eager to see if your oasis delivers the goods.
Laser Targeting Your Dream Clients, Not Random Tourists
But SEO isn’t just about attracting a crowd. It’s about attracting the right kind of crowd – the ones who are already halfway sold on what you do. By using the lingo people actually search for (keywords!), you basically become a human (or website) beacon for those actively seeking the solutions you provide. No more wasted pitches to people who just wandered in by accident. SEO brings you pre-qualified leads who are hot on your trail and ready to become raving fans (and hopefully, paying clients!).
The Google Stamp of Approval: From Underdog to Authority
The higher you rank on search engines, the more it’s like Google throws a spotlight on you and declares, “This website is legit!” This translates into a massive boost of trust and credibility with potential clients. They see you as an authority in your field, someone who has the answers they need. That trust factor is like gold – it makes them far more likely to choose you over some random competitor hiding in the shadows of the search results.
The #1 Spot: The Google Goldmine
Okay, ranking high on search engines is a win, but the ultimate prize is the coveted #1 spot. Here’s the thing: most people are lazy searchers, only clicking on the first few results. So, the higher you rank, the more clicks you score, which translates into a dramatic increase in website traffic – basically, more people checking out your virtual storefront.
Why Hiring an SEO Wizard like local SEO experts is Like Getting a Genie in a Bottle
Let’s be honest, SEO can be a bit of a magic trick. Search engine rules change faster than you can say “algorithm update,” and keeping up takes some serious wizardry. That’s why getting an SEO wizard on your team is a game-changer. They’re like digital sorcerers who constantly stay updated on the latest SEO spells and keep your website optimized for maximum visibility.
They Speak Tech, You Speak Business: The Dream Duo
The thing is, SEO involves some technical mumbo jumbo about website structure that would leave your head spinning. Your SEO wizard tackles all that magic, freeing you up to focus on what you do best – running your business and delivering stellar service to your clients. Plus, they use fancy data spells to track your progress, pinpoint areas for improvement, and constantly refine your SEO strategy for even better results.
Investing in SEO is like investing in a client magnet. By partnering with an SEO expert, you’ve unlocked the goldmine of search engines and now attract a steady stream of qualified leads, ready to be converted into loyal clients. So, ditch the outdated hustle and embrace the SEO revolution. Trust me, your business (and your sanity) will thank you for it.



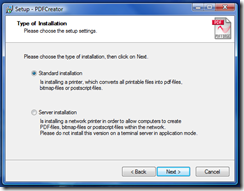
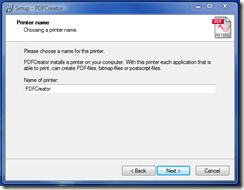
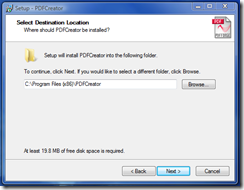
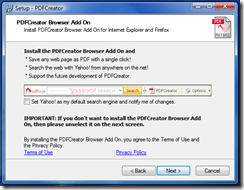
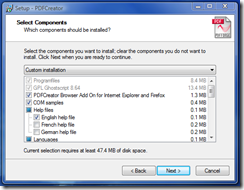
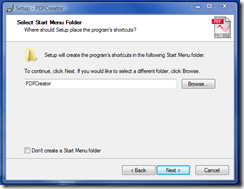
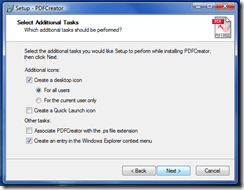
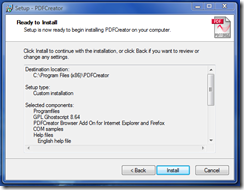

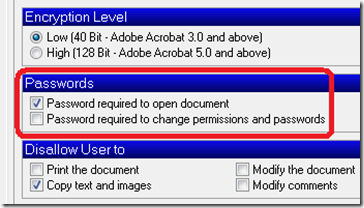
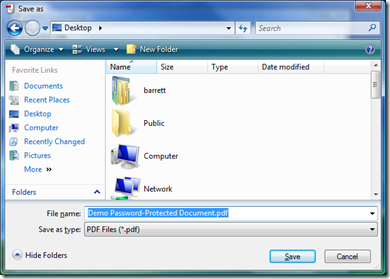

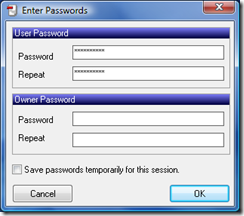
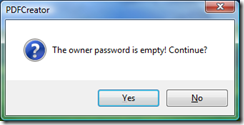

 According to the
According to the  Usually, technology and convergence of digital devices are wonderful things. But when a Best Buy Geek Squad employee abuses technology to *allegedly* use his cell phone to
Usually, technology and convergence of digital devices are wonderful things. But when a Best Buy Geek Squad employee abuses technology to *allegedly* use his cell phone to  How many new viruses come out per month? Back in the day we quoted 300 per month, then 400. And today
How many new viruses come out per month? Back in the day we quoted 300 per month, then 400. And today  Breaking the law just got even easier kiddos. Now any idiot with $59.95 can violate trust between parents & kids, spouses, employees or co-workers by simply plugging in a USB stick.
Breaking the law just got even easier kiddos. Now any idiot with $59.95 can violate trust between parents & kids, spouses, employees or co-workers by simply plugging in a USB stick. So far, 2007 has not been a very good year for Cisco. Yesterday they announced two more vulnerabilites in their Internetwork Operating System (IOS) – that’s 5 this year if my count is correct. And today they announced vulnerabilites in some PIX and ASA appliances:
So far, 2007 has not been a very good year for Cisco. Yesterday they announced two more vulnerabilites in their Internetwork Operating System (IOS) – that’s 5 this year if my count is correct. And today they announced vulnerabilites in some PIX and ASA appliances: